forked from go-gitea/gitea
-
Notifications
You must be signed in to change notification settings - Fork 1
New issue
Have a question about this project? Sign up for a free GitHub account to open an issue and contact its maintainers and the community.
By clicking “Sign up for GitHub”, you agree to our terms of service and privacy statement. We’ll occasionally send you account related emails.
Already on GitHub? Sign in to your account
Fork updates from go-gitea/gitea main #63
Open
github-actions
wants to merge
4,505
commits into
kitspace:main
Choose a base branch
from
go-gitea:main
base: main
Could not load branches
Branch not found: {{ refName }}
Loading
Could not load tags
Nothing to show
Loading
Are you sure you want to change the base?
Some commits from the old base branch may be removed from the timeline,
and old review comments may become outdated.
+314,322
−353,853
Conversation
This file contains bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
…#32528) - Move models/GetForks to services/FindForks - Add doer as a parameter of FindForks to check permissions - Slight performance optimization for get forks API with batch loading of repository units - Add tests for forking repository to organizations --------- Co-authored-by: wxiaoguang <wxiaoguang@gmail.com>
Remove unmaintainable sanitizer rules. No need to add special "class" regexp rules anymore, use RenderInternal.SafeAttr instead, more details (and examples) are in the tests
This makes `/login/oauth/authorize` behave the same way as the `/login/oauth/userinfo` endpoint.
When opening the latest code in **Gitpod** and running `make lint-backend`, the following error occurs: ```bash gitpod /workspace/gitea (main) $ make lint-backend go run github.com/golangci/golangci-lint/cmd/golangci-lint@v1.60.3 run # internal/profilerecord compile: version "go1.23.1" does not match go tool version "go1.22.9" # internal/goarch compile: version "go1.23.1" does not match go tool version "go1.22.9" # unicode/utf8 compile: version "go1.23.1" does not match go tool version "go1.22.9" # internal/coverage/rtcov compile: version "go1.23.1" does not match go tool version "go1.22.9" # internal/byteorder compile: version "go1.23.1" does not match go tool version "go1.22.9" # cmp compile: version "go1.23.1" does not match go tool version "go1.22.9" # internal/itoa compile: version "go1.23.1" does not match go tool version "go1.22.9" # internal/race compile: version "go1.23.1" does not match go tool version "go1.22.9" # internal/goos compile: version "go1.23.1" does not match go tool version "go1.22.9" # internal/unsafeheader compile: version "go1.23.1" does not match go tool version "go1.22.9" # unicode compile: version "go1.23.1" does not match go tool version "go1.22.9" # internal/godebugs compile: version "go1.23.1" does not match go tool version "go1.22.9" # internal/asan compile: version "go1.23.1" does not match go tool version "go1.22.9" # math/bits compile: version "go1.23.1" does not match go tool version "go1.22.9" # internal/goexperiment compile: version "go1.23.1" does not match go tool version "go1.22.9" # internal/msan compile: version "go1.23.1" does not match go tool version "go1.22.9" # internal/runtime/atomic compile: version "go1.23.1" does not match go tool version "go1.22.9" # sync/atomic compile: version "go1.23.1" does not match go tool version "go1.22.9" # internal/runtime/syscall compile: version "go1.23.1" does not match go tool version "go1.22.9" # crypto/internal/alias compile: version "go1.23.1" does not match go tool version "go1.22.9" # encoding compile: version "go1.23.1" does not match go tool version "go1.22.9" # log/internal compile: version "go1.23.1" does not match go tool version "go1.22.9" # vendor/golang.org/x/crypto/cryptobyte/asn1 compile: version "go1.23.1" does not match go tool version "go1.22.9" # github.com/golangci/golangci-lint/pkg/exitcodes compile: version "go1.23.1" does not match go tool version "go1.22.9" # internal/cpu compile: version "go1.23.1" does not match go tool version "go1.22.9" # unicode/utf16 compile: version "go1.23.1" does not match go tool version "go1.22.9" # container/list compile: version "go1.23.1" does not match go tool version "go1.22.9" # crypto/subtle compile: version "go1.23.1" does not match go tool version "go1.22.9" # internal/goversion compile: version "go1.23.1" does not match go tool version "go1.22.9" # golang.org/x/exp/maps compile: version "go1.23.1" does not match go tool version "go1.22.9" # github.com/ccojocar/zxcvbn-go/match compile: version "go1.23.1" does not match go tool version "go1.22.9" # golang.org/x/exp/constraints compile: version "go1.23.1" does not match go tool version "go1.22.9" # golang.org/x/tools/internal/packagesinternal compile: version "go1.23.1" does not match go tool version "go1.22.9" # github.com/quasilyte/go-ruleguard/dsl/types compile: version "go1.23.1" does not match go tool version "go1.22.9" # vendor/golang.org/x/crypto/internal/alias compile: version "go1.23.1" does not match go tool version "go1.22.9" # internal/nettrace compile: version "go1.23.1" does not match go tool version "go1.22.9" # github.com/google/go-cmp/cmp/internal/flags compile: version "go1.23.1" does not match go tool version "go1.22.9" # github.com/gobwas/glob/util/runes compile: version "go1.23.1" does not match go tool version "go1.22.9" # internal/platform compile: version "go1.23.1" does not match go tool version "go1.22.9" # crypto/internal/boring/sig compile: version "go1.23.1" does not match go tool version "go1.22.9" # github.com/quasilyte/gogrep/internal/stdinfo compile: version "go1.23.1" does not match go tool version "go1.22.9" # github.com/daixiang0/gci/pkg/utils compile: version "go1.23.1" does not match go tool version "go1.22.9" # github.com/quasilyte/stdinfo compile: version "go1.23.1" does not match go tool version "go1.22.9" # github.com/Antonboom/testifylint/internal/testify compile: version "go1.23.1" does not match go tool version "go1.22.9" # hash/maphash compile: version "go1.23.1" does not match go tool version "go1.22.9" # github.com/nunnatsa/ginkgolinter/version compile: version "go1.23.1" does not match go tool version "go1.22.9" # google.golang.org/protobuf/internal/flags compile: version "go1.23.1" does not match go tool version "go1.22.9" make: *** [Makefile:413: lint-go] Error 1 ```
PushMirrors only be used in the repository setting page. So it should not be loaded on every repository page.
 Highlight the path of the configuration file with a label-style emphasis and provide a quick copy button.
Found while working on #32433. This branch will never be executed because we have would have already made the same check a couple lines above.
…ecification (#32578) This PR adds support for the HTTP POST requests to `/userinfo` endpoint. While the OpenID Core specification says both are supported and recommends using HTTP GET. ref: https://openid.net/specs/openid-connect-core-1_0.html#UserInfo
We have some actions that leverage the Gitea API that began receiving 401 errors, with a message that the user was not found. These actions use the `ACTIONS_RUNTIME_TOKEN` env var in the actions job to authenticate with the Gitea API. The format of this env var in actions jobs changed with /pull/28885 to be a JWT (with a corresponding update to `act_runner`) Since it was a JWT, the OAuth parsing logic attempted to parse it as an OAuth token, and would return user not found, instead of falling back to look up the running task and assigning it to the actions user. Make ACTIONS_RUNTIME_TOKEN in action runners could be used, attempting to parse Oauth JWTs. The code to parse potential old `ACTION_RUNTIME_TOKEN` was kept in case someone is running an older version of act_runner that doesn't support the Actions JWT.
Fix #32568, parse `.gitmodules` correctly --------- Co-authored-by: wxiaoguang <wxiaoguang@gmail.com>
Thank you for @wxiaoguang's reminders and suggestions: #32558 (comment)
1. remove duplicate dividers 2. align reviewer items 3. merge & remove unused CSS styles Before: <details>   </details> After: <details>    </details>
Also adds a tooltip which is replicated to the same button in the diff box. Fixes: #32583
When running e2e tests on flaky networks, gravatar can cause a timeout and test failures. Turn off, and populate avatars on e2e test suite run to make them reliable.
Fixes around 30 or so typescript errors. No runtime changes.
Base branch deleted  branch deleted comment  Head branch deleted 
…ess (#32573) Resolve #31609 This PR was initiated following my personal research to find the lightest possible Single Sign-On solution for self-hosted setups. The existing solutions often seemed too enterprise-oriented, involving many moving parts and services, demanding significant resources while promising planetary-scale capabilities. Others were adequate in supporting basic OAuth2 flows but lacked proper user management features, such as a change password UI. Gitea hits the sweet spot for me, provided it supports more granular access permissions for resources under users who accept the OAuth2 application. This PR aims to introduce granularity in handling user resources as nonintrusively and simply as possible. It allows third parties to inform users about their intent to not ask for the full access and instead request a specific, reduced scope. If the provided scopes are **only** the typical ones for OIDC/OAuth2—`openid`, `profile`, `email`, and `groups`—everything remains unchanged (currently full access to user's resources). Additionally, this PR supports processing scopes already introduced with [personal tokens](https://docs.gitea.com/development/oauth2-provider#scopes) (e.g. `read:user`, `write:issue`, `read:group`, `write:repository`...) Personal tokens define scopes around specific resources: user info, repositories, issues, packages, organizations, notifications, miscellaneous, admin, and activitypub, with access delineated by read and/or write permissions. The initial case I wanted to address was to have Gitea act as an OAuth2 Identity Provider. To achieve that, with this PR, I would only add `openid public-only` to provide access token to the third party to authenticate the Gitea's user but no further access to the API and users resources. Another example: if a third party wanted to interact solely with Issues, it would need to add `read:user` (for authorization) and `read:issue`/`write:issue` to manage Issues. My approach is based on my understanding of how scopes can be utilized, supported by examples like [Sample Use Cases: Scopes and Claims](https://auth0.com/docs/get-started/apis/scopes/sample-use-cases-scopes-and-claims) on auth0.com. I renamed `CheckOAuthAccessToken` to `GetOAuthAccessTokenScopeAndUserID` so now it returns AccessTokenScope and user's ID. In the case of additional scopes in `userIDFromToken` the default `all` would be reduced to whatever was asked via those scopes. The main difference is the opportunity to reduce the permissions from `all`, as is currently the case, to what is provided by the additional scopes described above. Screenshots: 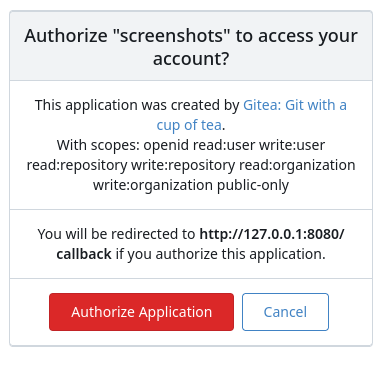    --------- Co-authored-by: wxiaoguang <wxiaoguang@gmail.com>
Style unification for the issue_management area (consistent across the layout before:    after:  --------- Co-authored-by: wxiaoguang <wxiaoguang@gmail.com>
This PR mainly moves some code and introduces `RenderContext.WithXxx` functions
Fix issues with inconsistent spacing in areas where the branch_dropdown component is used. before:   after: 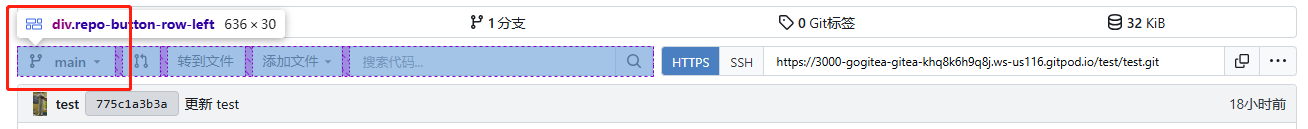 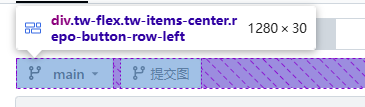 --------- Co-authored-by: wxiaoguang <wxiaoguang@gmail.com>
This PR adds a mock runner to test more actions features.
user with read permission should also can create agit flow pull request. looks this logic was broken in #31033 this pull request try fix it and add test code. --------- Signed-off-by: a1012112796 <1012112796@qq.com> Co-authored-by: wxiaoguang <wxiaoguang@gmail.com>
The new code structure is easier to make more improvements or refactor, for example: change the colors to de-emphasize more, or design some new layouts. --------- Co-authored-by: silverwind <me@silverwind.io> Co-authored-by: wxiaoguang <wxiaoguang@gmail.com>
A repository with no issue will display a random number on activities page. This is caused by wrong usage of `And` and `Or`. 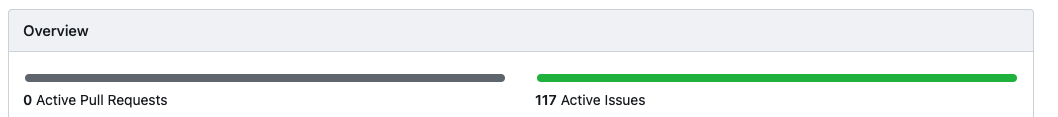
And fix a regression bug for comment content editing. Now 11 "import jquery" files left
…32997) #### Before 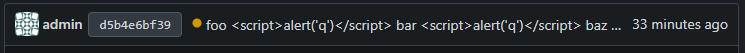 #### After  ## Edit: I found an issue on mobile view and changed the code as using flex gap   --------- Co-authored-by: wxiaoguang <wxiaoguang@gmail.com>
### Before  ### After 
1. fix incorrect tests, for example: BeanExists doesn't do assert and shouldn't be used 2. remove unnecessary test functions 3. introduce DumpQueryResult to help to see the database rows during test (at least I need it) ``` ====== DumpQueryResult: SELECT * FROM action_runner_token ====== - # row[0] id: 1 token: xeiWBL5kuTYxGPynHCqQdoeYmJAeG3IzGXCYTrDX owner_id: 0 ... ```
Adds test for expected behavior Closes: #33013
Fixes #33017 Avatar should only have offset if the `Comment` has `Content` or `Attachment` to align with the speech bubble. --------- Co-authored-by: wxiaoguang <wxiaoguang@gmail.com>
…d from latest commit cache (#32987) The latest commit cache is currently used only for listing tree files. However, a cold start may take longer than directly invoking the Git command. This PR addresses the issue of slow response times when accessing raw files, improving performance in such scenarios. ```log gitea.log:105521:2024/12/23 08:22:18 ...eb/routing/logger.go:68:func1() [W] router: slow GET /xxxx/xxxxxx/raw/commit/xxxxxxxxxxxxxxxxxxxxxxxxxxx/.editorconfig for 172.18.0.5:53252, elapsed 3526.8ms @ repo/download.go:117(repo.SingleDownload) ```
To help binary size and testing performance
Closes #25898 The problem was that the default settings weren't being loaded --------- Signed-off-by: cassiozareck <cassiomilczareck@gmail.com> Co-authored-by: Lunny Xiao <xiaolunwen@gmail.com> Co-authored-by: wxiaoguang <wxiaoguang@gmail.com>
This PR removed the dependency of `github.com/aws/aws-sdk-go/aws` Patially fix for #33023
No code change. Extract from #32178
Fix: #31980 --------- Co-authored-by: wxiaoguang <wxiaoguang@gmail.com>
Sign up for free
to join this conversation on GitHub.
Already have an account?
Sign in to comment
Add this suggestion to a batch that can be applied as a single commit.
This suggestion is invalid because no changes were made to the code.
Suggestions cannot be applied while the pull request is closed.
Suggestions cannot be applied while viewing a subset of changes.
Only one suggestion per line can be applied in a batch.
Add this suggestion to a batch that can be applied as a single commit.
Applying suggestions on deleted lines is not supported.
You must change the existing code in this line in order to create a valid suggestion.
Outdated suggestions cannot be applied.
This suggestion has been applied or marked resolved.
Suggestions cannot be applied from pending reviews.
Suggestions cannot be applied on multi-line comments.
Suggestions cannot be applied while the pull request is queued to merge.
Suggestion cannot be applied right now. Please check back later.
No description provided.